Investigate
leaks of text data leaks of document leaks of emails insider threats
G-71 Security is a solution designed to deter leaks of confidential documents using invisible watermarks, enabling swift and successful leak investigations—even when information is compromised through smartphone photography.
Cost of insider threats
How much are you currently spending on combating insider leaks?
*Ponemon Institute, 2023
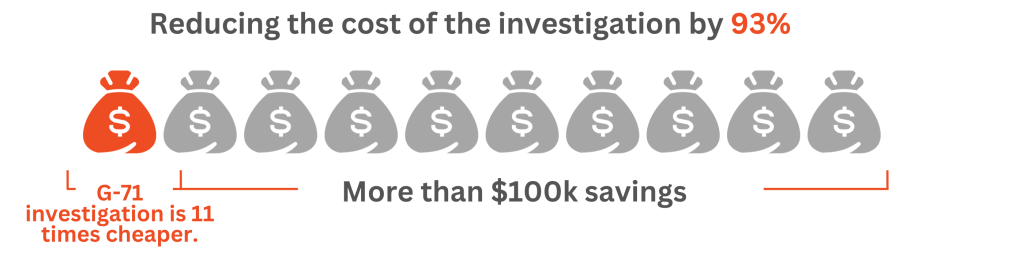
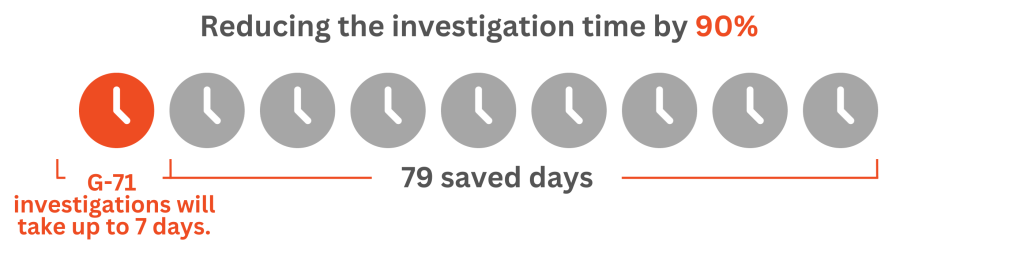
Imagine an 8x faster, 10x cheaper
leak investigation.
Reduce your insider threat mitigation costs with G-71.

Quickly investigate text data leaks and identify the source
In the event of a data breach, regardless of the type of information leaked—be it contacts, presentations, intellectual property materials, or any other sensitive content—whether it was obtained through screenshots, personal smartphone photos, or printed and subsequently published, our system will swiftly identify the source of the breach. This is made possible through the use of invisible watermark on all your sensitive textual data. Even those formats of confidential material leaks that were previously challenging to investigate due to limited capabilities, such as when someone takes a photo of a sensitive screen, are now possible and accessible.

Start marking your text data in advance
Enable the automatic invisible watermarking feature to proactively protect your documents, emails, intellectual property, confidential text data, and sensitive information using invisible G-71 marks. The marking is applied automatically as an invisible fingerprint injection and does not affect the quality of the displayed content, unlike visible watermarks. This process has no impact on your workflow, and operates in the background. You can choose which textual data to mark, whether it's email attachments, printed documents, or content on your website or internal portal. Simply initiate the marking quickly and rest assured that in case of a potential breach, you have everything marked and ready for fingerprint detection and AI-investigation.
To conduct an investigation in case of a leak, start marking your content today.
Proactive measures are necessary for various types of textual data, enabling you to be well-prepared in the event of a leak and to conduct a prompt AI-investigation.
Confidential Documents
Prevent potential leaks of your sensitive documents (contracts, agreements, presentations, etc.) stored in your document management system, in your cloud storage, and in any other systems within your company.
Sensitive Emails
When sending sensitive information to third parties, invisibly mark your email attachments of any text formats or text within the body of the email using invisible G-71 labeling.
Content Security
Secure your website or portal's content to prevent any breaches, even through the copy-paste approach, covering articles, restricted/internal announcements, and premium paywall articles.
Internal Security
Protect your confidential information within internal systems, such as medical portals, educational testing systems, patient records, or government organizations' private portals.
HOW MUCH DOES IT COST?
Pricing
-
Unlimited users
-
Unlimited invisible watermarking capacity
-
All hosted on your infrastructure
-
There's no need to overpay
-
Unlimited AI-investigations
HOW DOES MARKING HELP TO CONDUCT INVESTIGATIONS?
About G-71 Invisible Watermarks
Here are three reasons to choose the G-71 fingerprint injection to mitigate insider leaks.
Any formats
You can label any text data and screen forms, including documents, presentations, email bodies, internal & external content.
Easy to use
No training needed; marking is automatic and integrated in real time with various systems (EDMS, cloud storages, internal apps, etc).
Invisible Watermark
Fingerprint injection is invisible to the naked eye; only G-71 can recognize it via AI-detection, even in leaked photos or screenshots.